Question 34:
Device event logs sources from MDM software as follows:
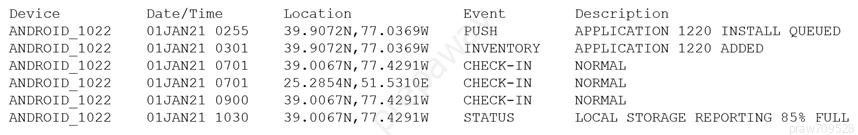
Which of the following security concerns and response actions would BEST address the risks posed by the device in the logs?
Answer options:
A. Malicious installation of an application; change the MDM configuration to remove application ID 1220. B. Resource leak; recover the device for analysis and clean up the local storage. C. Impossible travel; disable the device`s account and access while investigating. D. Falsified status reporting; remotely wipe the device.