Question 8:
A security analyst is reviewing the following output:
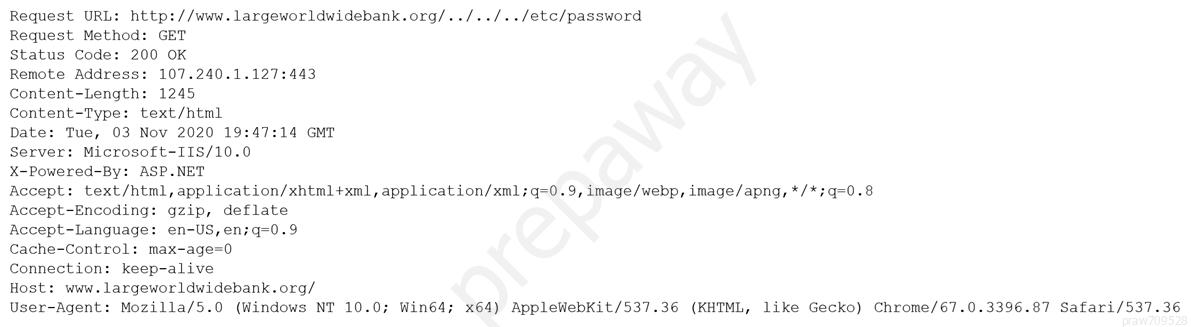
Which of the following would BEST mitigate this type of attack?
Answer options:
A. Installing a network firewall B. Placing a WAF inline C. Implementing an IDS D. Deploying a honeypot